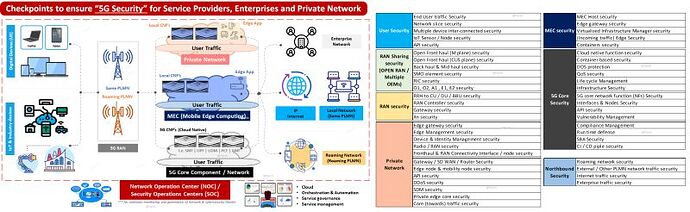
|| 5G Security End to End Architecture ||
Ensuring 5G security across service providers, enterprises, and private networks involves several critical checkpoints, below is end to end architecture with all the possible areas for which security check is required.
Some of the key points to be noted:-
Access control measures must be stringent for devices and network nodes.
Implementing robust authentication protocols and encryption techniques for data transmission.
Secure configuration and management of network devices are crucial
Intrusion detection systems to promptly identify and respond to potential threats.
Constant monitoring, regular security updates, and the enforcement of security policies at various network points/nodes.
Protection against DDoS attacks and secure APIs for inter-device communication.
Compliance with industry standards and regulatory requirements.
Below are list of security across nodes :-
User Security
End User traffic Security
Network slice security
Multiple device inter-connected security
IoT Sensor / Node security
API security
RAN Sharing security (OPEN RAN / Multiple OEMs)
Open Front haul (M plane) security
Open Front haul (CUS plane) security
Back haul & Mid haul security
SMO element security
RIC security
O1, O2, A1 , E1, E2 security
RAN security
RRH to CU / DU / BBU security
RAN Controller security
Gateway security
Xn security
#PrivateNetwork
Edge gateway security
Edge Management security
Device & Identity Management security
#Radio / RAN security
Fronthaul & RAN Connectivity Interface / node security
Gateway / #SDWAN / #Router Security
Edge & mobility node security
API security
DDoS security
SDM security
Private edge core security
Core (towards) traffic security
MEC security
MEC Host & Edge gateway security
Virtualized Infrastructure Manager security
(Incoming traffic) Edge Security
Containers security
#5GCore Security
Cloud native function security
Container based security
DOS protection
QoS security
Life cycle Management
Infrastructure Security
5G core network function (NFs) Security
Interfaces & Nodes Security
API security
Vulnerability Management
Compliance Management
Run time defense
SBA Security
CI / CD pipe security
Northbound Security
Roaming NW security
External / Other PLMN NW traffic security
Internet traffic security
Enterprise traffic security
Follow me for telecom & automation related post.
Read more → 5G Security End to End Architecture