Can WiFi be tricked by fake beacons?
Not in Wi-Fi 7!
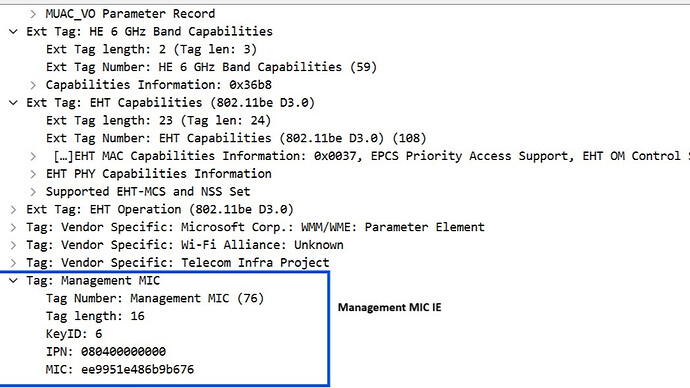
Discover how MMIC protects networks from stealthy attacks.
In previous Wi-Fi generations, beacon frames were vulnerable to spoofing and manipulation, leading to potential security threats. Attackers could:
- Inject fake beacons to mislead clients.
- Modify BSS parameters to disrupt roaming decisions.
- Trigger false channel switch announcements (CSA attacks) to cause unnecessary client disconnections.
To solve this, Wi-Fi 7 (EHT, 802.11be) introduces Management MIC (MMIC), ensuring that critical management fields remain authentic and protected from tampering.
MMIC secures essential fields in the EHT Beacon frame, such as:
- BSS Parameters – Prevents unauthorized modifications to network settings.
- Traffic Indication Map (TIM) – Ensures accurate delivery of buffered data notifications.
- Channel Switch Announcement (CSA) – Blocks attackers from misleading clients with false channel switch requests.
LinkedIn: ![]()